I was simulating in my active directory test environment on group policy misconfiguration issue and hence posting it here for reference.
If local admin users are pushed via GPO, Domain logged in users can just search for "Group.XML" or ".XML" file on their local system.
This files contains AES encrypted password, and fortunately Microsoft has published AES keys used to encrypt this password here
Push "localadmin" user via GPO - It's damn simple, just have to add user in Group Policy Management Editor > Computer Configuration > Preferences > Local User and Groups
Once you create localadmin user via GPO, it shows this alert - Password is discoverable
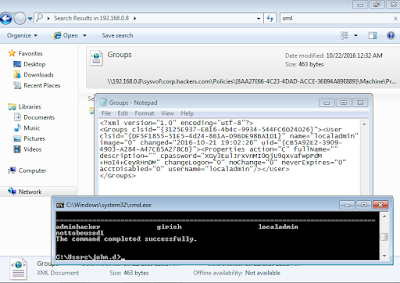
Once user is created, you can go to any workstation in your domain and just connect to domain controller via \\IP and search for .XML file.
We can clearly see encrypted password in file Groups.XML file.
I suppose, solution for this is pretty simple, you just have to remove user from control panel on domain controller.
Extracting password for "localadmin" using powershell script
You can find the script here
I know its pretty simple to execute, but all I wanted to check is actual AD configuration!
Thanks.




No comments:
Post a Comment