Hi,
It was fun playing Nullcon CTF 2015 challenges, and learnt lot of things over 2 days!
One of the challenge consist of interesting crypto attack known as "Length Extension Attack"
Referring this diagram from Wikipedia : http://en.wikipedia.org/wiki/Message_authentication_code

1. Sender has "Hash" i.e MAC & Message which will be sent to server.
2. Receiver receives MAC and Message
3. Receiver passes Message + Secret Key to algorithm = MAC
4. Receiver Compares new generated MAC with MAC received from Sender if matches message is authentic.
Nullcon pass at 10999 Rs
If you observe source code it has information - Hash + Message + Length of Secrete key (19)
Pass above information to Hashpum tool which will perform Length Extension Attack to generate new hash to buy our product in 0 Rs. by appending |0
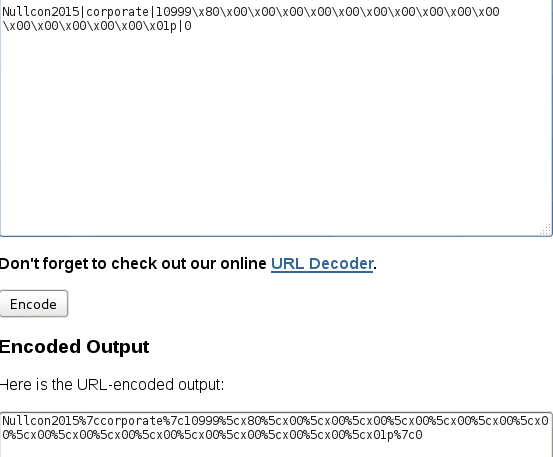
Message Format = Nullcon2015|Corporate|10999 i.e price
URL Encode new generated message from Hashpump and remove unnecessary characters "5cx"
Tamper data will show original Message & Hash
Tamper original Message and Hash with updated Hash and URL Encoded message
Forward HTTP request and That's It!.. You bought Nullcon Pass for 0 Rs.
This was interesting challenge and thought to post here on blog although CTF writ up is being published on official NullCon Site..
It was fun playing this CTF...and wish to learn more things going ahead!.
Regards,
eXpl0i13r