Dear All,
Found interesting challenge named "Metasploitable" at www.hackaserver.com/arena/training
and would like to share how to get root access on that server.
Of course I started with port scanning as everyone do!!! and below is interesting result!!!
 | |
| Port Scanning |
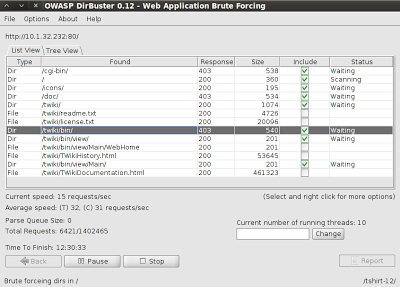
Found interesting results on port 80 through DirBuster tool, from
/pentest/web/dirbuster (Backtrack distrubution)
Next we will fireup metasploit to check if any working exploit for twiki and here is our result : (twiki_history)
Lets Exploit it!!!!
Vola!!..after exploitation we have shell with user "www-data" but we need r00t access and not this limited shell!...for this we need to check for privilege escalation exploits or chroot exploits, after a bit of research found that server is running with kernel 2.6.24 which is affected by Udev vulnerability, but need to confirm if udev is running or not...
Time to check for udev local privilege escalation exploits...
I have tried to check both but first exploits seems complicated and didn't work for me, so went for second exploit 8572.c, first we need to start apache server on our local machine and copy this 8572.c exploit to /var/www/ directory.
Note : you will find this exploit in /platforms/linux/local/ directory
after copying lets download this exploit from our Exploited servers shell using wget utility , in /tmp directory as it has write permissions!!!
Now its time to compile downloaded exploit
This exploit expects that /tmp/run file exists and contains necessary data as show in below screeshot, an which in turn creates shell file with root user and group.
Now we have exported necessary data in "run" file but if you directly run exploit with PID as parameter at this stage it won't work for you because run file does not have necessary permissions at this moment, which you will have to set manually "chmod 777 run"
Again one problem is if you have PID 2056 , we need to specify parameter as PID - 1 , if you check exploit code you will come to know why!!!
Lets confirm! if we are actually root or not!!
Finally we got root access!!....
This was really good exercise, I know most of genius have already exploited these challenges but still for newbie it will be a good start, looking forward to publish more interesting stuff soon, Keep visiting and Keep commenting let me know your feedback.












No comments:
Post a Comment