Hi,
Going one step further in learning Arduino UNO, I wanted to print word "HACK" on Display module with 4 Digit and 7 Segments, you can check specification here : Link
I was struggling to know how it works and which pins to connect where on Arduino board.
As its digital display we will use Digital pins from Arduino board from 1 to 13.
This is how segments are numbered on actual Display Unit from a to g
Now how do you set-up the Circuit?
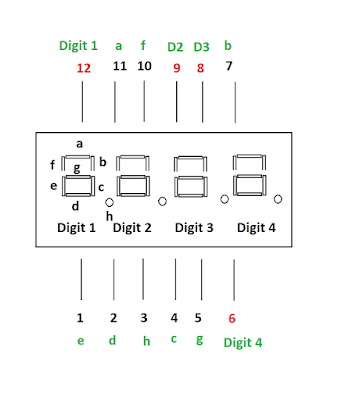
Pin structure and its functionality is as follows :
Key is Logic!....If you want to display anything on Digit 1 of display uni then you need to enable Arduino Pin 2 and set its voltage to HIGH and set other Digits to LOW
Core Program Logic
1. Turn on first digit, turn off all other digits
2. Turn on segments we need for first digit and set delay to 5
3. Turn off all digits, turn on second digit
4. Turn on segments we need for second digit and set delay to 5
5. Turn off all digits, turn on third digit
6. Turn on segment we need for third digit and set delay to 5
7. Turn off all digits, turn on fourth digit
8. Turn on all segments we need for fourth digit and set delay to 5
Hope this helps...!

















